September 21, 2022
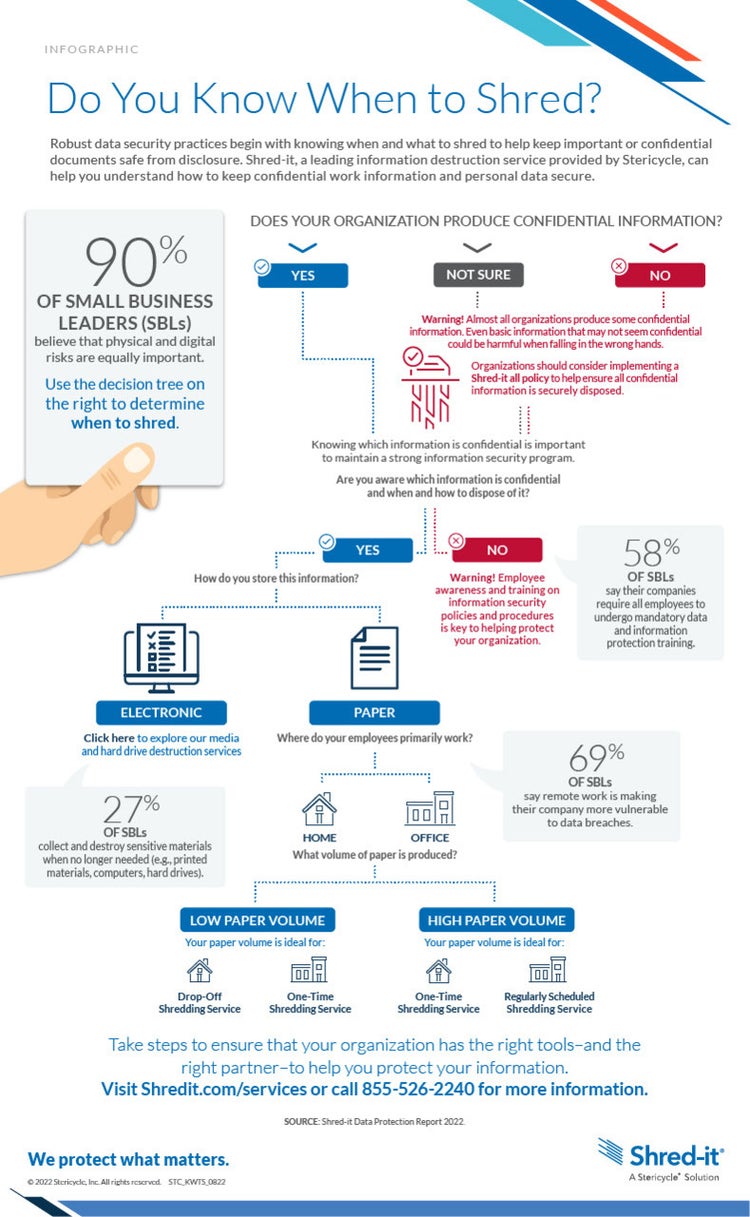
Knowing When to Shred: A Decision Tree
In an age where consumers care more about data privacy than ever before, information breaches can wreak havoc on businesses. Data breaches can damage corporate budgets and reputations and even put the future of a business in jeopardy. In fact, a recent study found that 60 percent of small to mid-size businesses close within six months of experiencing a data breach. Businesses should have strong data protection strategies in place to help avoid information security failures and retain consumer trust.
To help organizations and employees make the right data security choices, Shred-it, a Stericycle solution, has developed a guide and infographic to explain each step of the information destruction decision-making process.
Knowing Data: Determine What information Is Confidential
The term “confidential” can have multiple meanings depending on which industry a business belongs to and which regulations apply. However, most experts agree that information is considered “confidential” if it contains personally identifiable information (PII), such as addresses, social security numbers, private health information, or financial information. “Confidential” could also refer to private information related to legal proceedings or transactions.
Businesses of all sizes generate or collect at least some confidential information. For example, most companies store and use employee PII for payroll and emergency purposes. To help develop an effective and compliant data security strategy, leaders should evaluate the data their organizations produce or capture, identify what information is confidential and create a plan around it. If companies leave data storage unaddressed and unprotected, they could make themselves vulnerable to a data breach.
Leaders can build a better understanding of what types of, and how much, confidential data their organization stores by answering five essential data management questions. When identifying these confidential items, leaders should also consider the legal and regulatory requirements associated with the retention or disposal of confidential information.
Implementing Policies and Procedures
Once leaders have identified which confidential information their organization collects and stores, they should establish specific, actionable data protection policies for their workforce. Shred-it recommends three policies for most businesses:
Shred-it All Policy: A Shred-it all policy requires all documents in the workplace to be routinely discarded in a secure shredding bin when no longer needed or required to be retained. This policy might also include scheduling regular shredding services.
Clean Desk Policy: A clean desk policy requires employees to clear any sensitive information whenever they leave their desk. This can help reduce clutter and help ensure that sensitive data is not overlooked and left in vulnerable places. To implement a clean desk policy, organizations should:
- Provide lockable storage.
- Encourage employees to close digital documents before leaving their desks.
- Follow the Three Ps of office organization: (1) plan the workday ahead, (2) protect confidential information always, and (3) pick up all items from the workspace at the end of the day.
Remote Work Data Security Policy: Many workplaces lack a remote work data security policy despite the massive increase in employees working remotely since the start of the COVID-19 pandemic. Leaders should ensure that there are well-established company protocols in place for employees to follow when handling their documents or data. If appropriate for business and employees' needs, leaders can consider setting up residential shredding services as a part of their remote working policy.
Employee Training: Fostering Data Security Champions
Comprehensive training and education around physical and digital data management can help establish a culture of information security in the workplace and establish a first line of defense against attacks and breaches. Shred-it offers guidance towards fostering a culture of information security in the workplace through several suggested strategies, including developing educational materials, providing physical reminders, auditing workspaces, and recognizing successful employees.
Empower Your Business: Find the Right Service for Your Needs
There are many services available through Shred-it to assist organizations in the disposal of confidential information. When choosing a company to partner with, leaders need to be sure that their documents remain safe and secure from the moment they leave the building to the moment they are destroyed. Shred-it’s services include:
- Drop Off Shredding Service: This solution is ideal for those with low paper volume. Home offices, small businesses, or individuals with shredding needs can locate the nearest drop-off location for their documents.
- Regularly Scheduled Shredding Service: Regular shredding services offer timely solutions to organizations with high paper volume. Businesses can have documents securely transported for destruction or shredded on-site with this option.
- One-Time Shredding Service: This solution is available for both low and high paper volumes. One-time paper shredding offers secure destruction of confidential information following a clean-out or other purge.
Learn more about which shredding services are most appropriate for your organization by downloading the Decision Tree infographic or visiting the services hub.